What are the three types of cryptography
Cryptography and its Types
It protects information and communications through codes so only those for whom the information is intended can read and process it. There are three main types of cryptography: symmetric key encryption, asymmetric key encryption, and public-key encryption.
What are the 3 steps of cryptography
Step 1: Encrypt the original message using symmetric key cryptography. Step 2: Encrypt the key used in step one using the receiver's public key i.e. using asymmetric key cryptography. Step 3: Send both the encrypted message and encrypted symmetric key to the receiver.
What are the 3 properties of cryptography
A function that maps a bit string of arbitrary length to a fixed length bit string and is expected to have the following three properties: 1) Collision resistance (see Collision resistance), 2) Preimage resistance (see Preimage resistance) and 3) Second preimage resistance (see Second preimage resistance).
What are 3 applications of cryptography
Applications of CryptographySecure communications. The most obvious use of cryptography, and the one that all of us use frequently, is encrypting communications between us and another system.End-to-end Encryption.Storing Data.Storing Passwords.Cryptography is hard.
What are the 4 concepts of cryptography
Cryptographic principles are the fundamental concepts and techniques that are used in the field of cryptography to secure communication and protect data. These principles include confidentiality, integrity, authentication, non-repudiation, and key management.
What are the 4 principles of cryptography
Data Confidentiality, Data Integrity, Authentication and Non-repudiation are core principles of modern-day cryptography. Confidentiality refers to certain rules and guidelines usually executed under confidentiality agreements which ensure that the information is restricted to certain people or places.
What is 3 layer encryption
Encryption on layer 3 of the OSI model enables the secure transmission of IP-packets via a public transport network. Usually the encryption realized software-based in the router or in the end device.
What are the 2 types of cryptography
Cryptography is broadly classified into two categories: Symmetric key Cryptography and Asymmetric key Cryptography (popularly known as public key cryptography). Now Symmetric key Cryptography is further categorized as Classical Cryptography and Modern Cryptography.
What are 4 uses of cryptography
Abstract. 'Uses of cryptography' reviews the applications for cryptographic algorithms other than for confidentiality. Cryptography is now used for data integrity, entity authentication, data origin authentication, and non-repudiation.
What are the two main types of cryptography
Cryptography is broadly classified into two categories: Symmetric key Cryptography and Asymmetric key Cryptography (popularly known as public key cryptography).
What is the basic of cryptography
Cryptography, at its most fundamental level, requires two steps: encryption and decryption. The encryption process uses a cipher in order to encrypt plaintext and turn it into ciphertext. Decryption, on the other hand, applies that same cipher to turn the ciphertext back into plaintext.
What are the 5 concepts of cryptography
Cryptographic principles are the fundamental concepts and techniques that are used in the field of cryptography to secure communication and protect data. These principles include confidentiality, integrity, authentication, non-repudiation, and key management.
What are the four 4 most secure encryption techniques
11. What are the 4 basic types of encryption systemsAdvanced Encryption Standard (AES)Triple DES.Blowfish.Rivest-Shamir-Adleman (RSA)
What is Layer 4 encryption
The Certes Layer 4 solution is an encryption management technology that delivers on our promise of Certes Networks Provable Security™ to quantify and measure the effectiveness of a security strategy. The Certes Layer 4 technology enables encryption of data in transit at Layer 3 and Layer 4.
What is layer 3 technology
Layer 3 is the network layer and its protocol is the Internet Protocol or IP. Devices in an IP network are identified by an IP address, which can be dynamically assigned and may change over time.
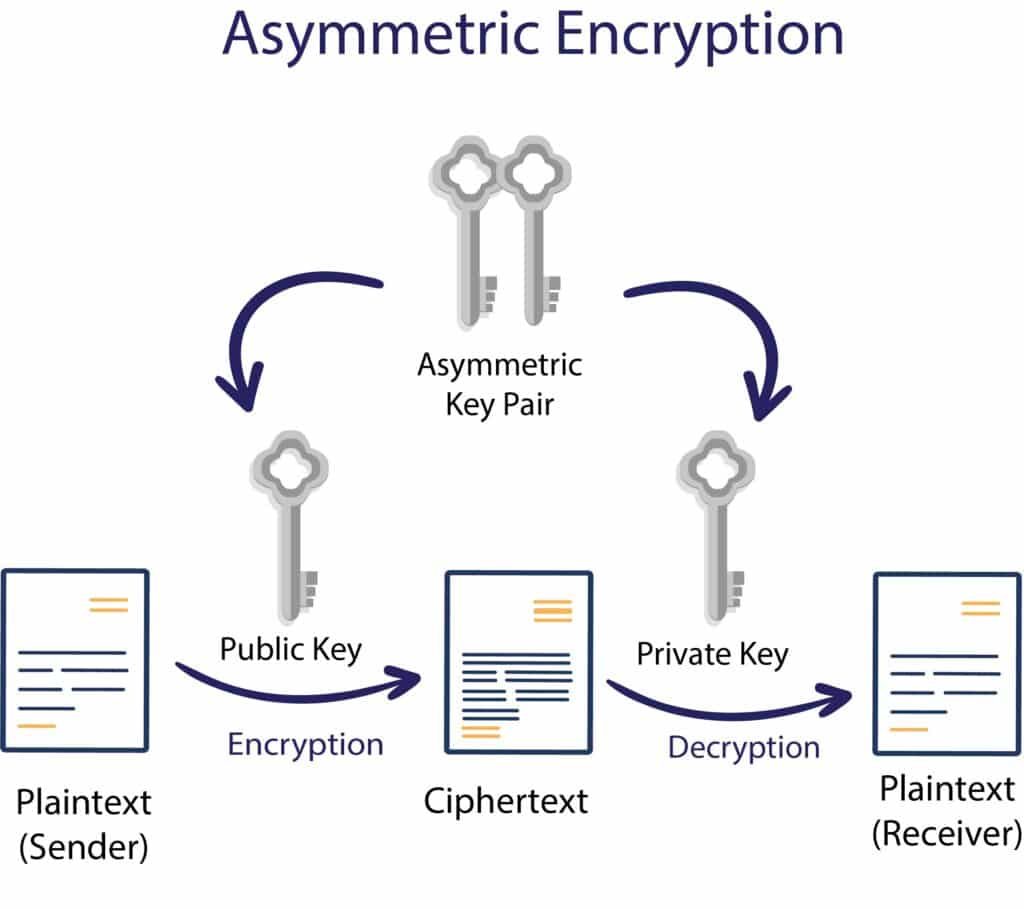
What are the cryptography types
Types Of CryptographySymmetric Encryption: It is a cryptographic type that utilizes a single key for both encryption and decryption.Hash Function: Hash functions are mathematical functions used in cryptography to convert numerical input data into another compressed numerical value.Asymmetric Encryption:
What are the 2 principles of public-key cryptography
Principles of Public Key Cryptosystem. There are two basic principles of any cryptosystem i.e. confidentiality and authenticity. We have seen that the symmetric cryptosystem has a problem associated with these two principles.
What are the 4 pillars of cryptography
There are five pillars of cryptology:Confidentiality: keep communication private.Integrity: detect unauthorized alteration to communication.Authentication: confirm identity of sender.Authorization: establish level of access for trusted parties.Non-repudiation: prove that communication was received.
What type of cryptography is used today
Asymmetric key cryptography is also known as public-key cryptography, and it employs the use of two keys. This cryptography differs from and is more secure than symmetric key cryptography. In this system, each user encrypts and decrypts using two keys or a pair of keys (private key and public key).
What is level 4 encryption
Private keys can only enter or leave in encrypted form. Level 4: This level makes the physical security requirements more stringent, requiring the ability to be tamper-active, erasing the contents of the device if it detects various forms of environmental attack.
What are the 2 types of data encryption
There are two types of encryption in widespread use today: symmetric and asymmetric encryption. The name derives from whether or not the same key is used for encryption and decryption.
What is Layer 7 encryption
Encryption on layer 7
Any logic can be implemented in software, as long as both sender and receiver support it. The receiver does not need to decrypt data in the moment of reception, but can simply store it in encrypted form, or even forward it without having had a look .
Is TLS layer 4 or layer 7
Because TLS operates at Layers 4 through 7 of the OSI model, as opposed to Layer 3, which is the case with IPsec, each application and each communication flow between client and server must establish its own TLS session to gain authentication and data encryption benefits.
What is Layer 3 in cyber security
The Layer 3 approach to security looks at the entire network as a whole including edge devices (firewalls, routers, web servers, anything with public access), endpoints such as workstations along devices connected to the network including mobile phones to create an effective plan for security management.
What is a layer 3 blockchain
What Is Bitcoin Layer 3 Layer 3 is often referred to as the application layer. It is a layer that hosts DApps and the protocols that enable the apps. While some blockchains such as Ethereum or Solana (SOL) have a thriving variety of layer 3 apps, Bitcoin is not optimized to host such applications.