What are the qualities of a good backup
Obviously, in the best of all possible worlds, backups would be perfectly reliable, always available, easy to use, and really fast. In the real world, trade-offs must be made. For example, backups stored offsite are good for disaster recovery, but are not always available.
What is effective backup
A backup strategy is a plan made to ensure that essential business data is backed up and ready to restore if there is any kind of data loss. Organizations suffer from any downtime due to data loss, so it is crucial to minimize downtime as much as possible.
What are the most important things to backup
What Files Should You BackupPersonal Directories. Having a backup of your data is the most crucial thing to do.Projects. Keep a copy of any creative work, such as projects, you're currently working on in case anything happens to your computer or you lose it.Mails.Important Files.
What are the 3 types of backups
Types of BackupsFull backup: The most basic and comprehensive backup method, where all data is sent to another location.Incremental backup: Backs up all files that have changed since the last backup occurred.Differential backup: Backs up only copies of all files that have changed since the last full backup.
What are the three 3 factors to consider for successful backups
For backup strategies to be successful the process has to successfully execute in three areas; backup, recovery, and time. Backup, of course, is the task of copying data from the source servers to the backup destination.
What are the golden rules of backup
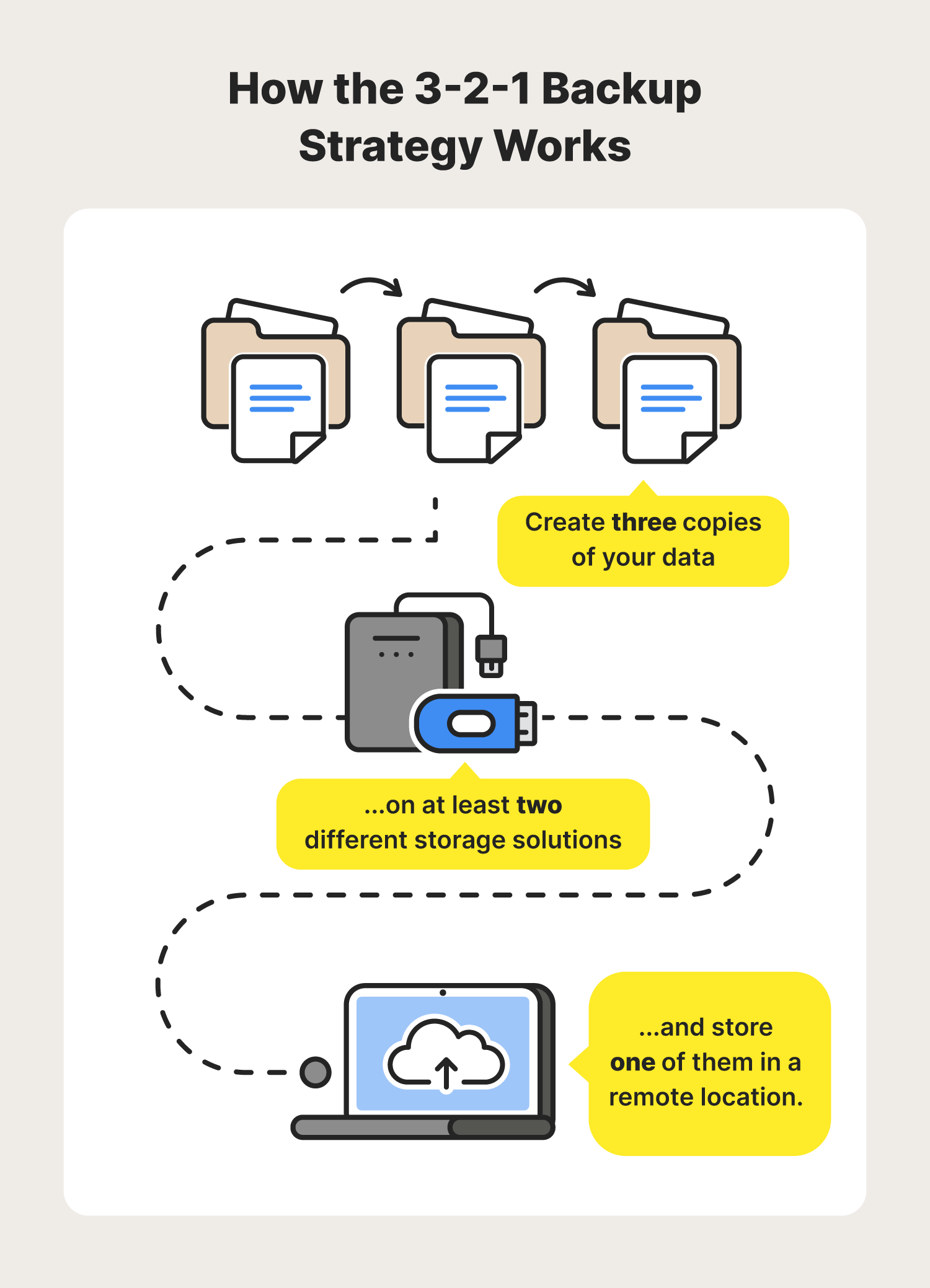
Follow the 3-2-1 Rule
This rule suggests that your business should do the following: Store a minimum of three copies of your data. Two of these backups should remain on separate storage media. One backup stays stored offsite, such as in the cloud.
What is the best type of backup
Full backups
The primary advantage to performing a full backup during every operation is that a complete copy of all data is available with a single set of media. This results in a minimal time to restore data, a metric known as a recovery time objective.
How do I make a successful backup
What makes a good backup Experts recommend the 3-2-1 rule for backup: three copies of your data, two local (on different devices) and one off-site. For most people, this means the original data on your computer, a backup on an external hard drive, and another on a cloud backup service.
Which type of backup is fastest
Incremental backups are completed quickly and require fewer resources. Disadvantage: While incremental backups have the fastest backup time, they also boast the slowest data recovery time.
What are 3 characteristics of a secure backup
Backups should be physically protected as well as encrypted, password protected, and restricted as to the ability to recover and restore to alternate locations.
What are the three components of a good backup plan
A good backup strategy has three parts: backups and archiving, disaster recovery, and business continuity. Periodic backups and archiving should be your first line of defense. When data is created or changed, your organization should back it up on a regular basis.
What is the best backup rule
According to the 3-2-1 backup rule, you should keep at least two backup copies to protect your data against natural disasters, accidental deletions, hardware failure and cyberattacks.
What storage is best for backup
Solid state drive (SSD) & flash drive (aka thumb drive, USB drive/stick) Flash drives and SSDs are the most efficient physical way to backup your system. Flash drives and solid state drives use flash technology to write and read data very quickly, making for speedy backups.
Which backup is most space efficient
Incremental backups are the most space efficient backup technique.
Which backup is most efficient
Incremental backups take the least space and time to perform than differential and full backups, but it's the most time-consuming out of all of the methods to restore a full system.
What is the 3 backup rule
The 3-2-1 backup strategy simply states that you should have 3 copies of your data (your production data and 2 backup copies) on two different media (disk and tape) with one copy off-site for disaster recovery.
What are the 3 basic requirements of information security
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
How do I make a good backup plan
Here are five steps you can take to establish a solid backup strategy:Define your backup needs.Budget for your backup plan.Choose a data backup vendor.Implement your data backup plan.Test your data backup plan.
What are the four 4 types of backup systems
The most common backup types are a full backup, incremental backup and differential backup. Other backup types include synthetic full backups and mirroring. In the debate over cloud vs. local backup, there are some types of backup that are better in certain locations.
What is 3-2-1 1 backup strategy
You may have heard of the 3-2-1 backup strategy. It means having at least three copies of your data, two local (on-site) but on different media (read: devices), and at least one copy off-site. We'll use “socialsecurity.
Is HDD or SSD better for backup
HDDs are the best when it comes to backups because of their high capacity and low cost per gigabyte.
What is the best backup approach
The 3-2-1 rule of backup states that organizations should keep three complete copies of their data, two of which are local but on different types of media, with at least one copy stored off site.
What is the most popular backup device
External Hard Drive
External hard drives are a popular choice for data backup due to their convenience and ease of use. These devices connect to your computer via USB or other connection types and offer a large amount of storage space for your data.
What are the 3 A’s of data security
Authentication, Authorization, and Accounting (AAA) is a three-process framework used to manage user access, enforce user policies and privileges, and measure the consumption of network resources.
What are the five 5 key features of information security
The U.S. Department of Defense has promulgated the Five Pillars of Information Assurance model that includes the protection of confidentiality, integrity, availability, authenticity, and non-repudiation of user data.